Introductions
Many antivirus vendors whitelist software, which is signed by valid digital certificates. They do that because there are gray areas to judge between normal software or malware. For example, some RDP software retrieves credentials from Windows registries, but the behavior is typically deemed as malicious. Due to these types of gray areas, if a piece of software is signed by valid digital certificates, then security controls may just bypass it, without scanning it.
However, according to CloudCoffer intelligence, many cyber criminals have been able to use these valid digital certificates to sign malware and do malicious behavior. It is happening in the worldwide now.
Under the circumstances, malware that is signed by valid digital certificates has been compromising organizations, without being noticed.
Analysis
CloudCoffer has found that in these days, malware is widely signed by valid digital signatures of corporations and exists in corporations. One example is that the digital certificate “F518FAD5DEC9E0500DA1C1598C4B0FFC0268B2D0” of a multinational technology company was stolen, and much malware has been signed by it. The following diagram shows the detailed information of the stolen digital signature.
Under the circumstances, malware that is signed by valid digital certificates has been compromising organizations, without being noticed.
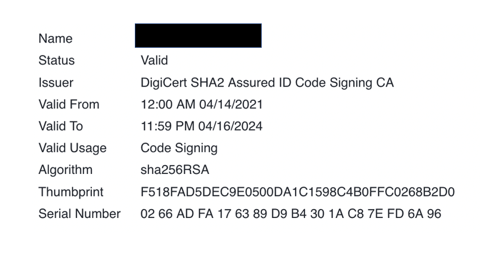
Diagram 1: Stolen digital signature from the multinational technology company
One hash value of the sample malware is “44da6217702a77c01ed9735e67d6fffee11de2298aaaea899ddbc39da26460e0.”
If victims are infected by the malware, attackers may read private messages, connect to C&C servers, and steal sensitive information from browsers, from the victims’ systems. The malware also tries downloading an executable file named “build.exe”, which connects the victim’s systems to 142.250.180.142, which is currently abused as a C&C server. The following diagram from “abuseipdb.com” shows 142.250.180.142 was reported to execute malicious behavior like “Fraud Orders”, “DDoS attack”, “Hacking”, etc.
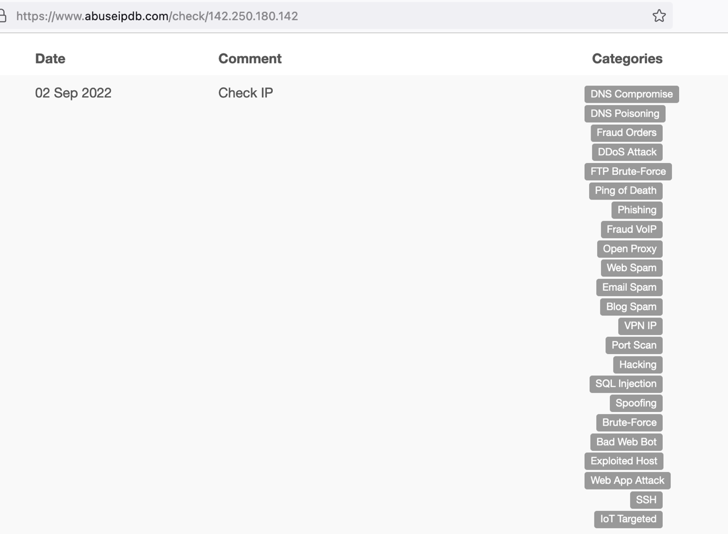
Diagram 2: abuseipdb.com shows that 142.250.180.142 is involved with many cyber criminal events.
In another example, the digital certificates of governments are leaked by 3rd development parties, and attackers have used the digital certificates to release malware. The attackers have sent internal sensitive information through root DNS, which’s IP address is 198.97.190.53. Because 198.97.190.53 is a root DNS, many security controls have also whitelisted it. Even if 198.97.190.53 is a root DNS, as the following diagram, it was reported to join cyber attacks from “abuseipdb.com”.
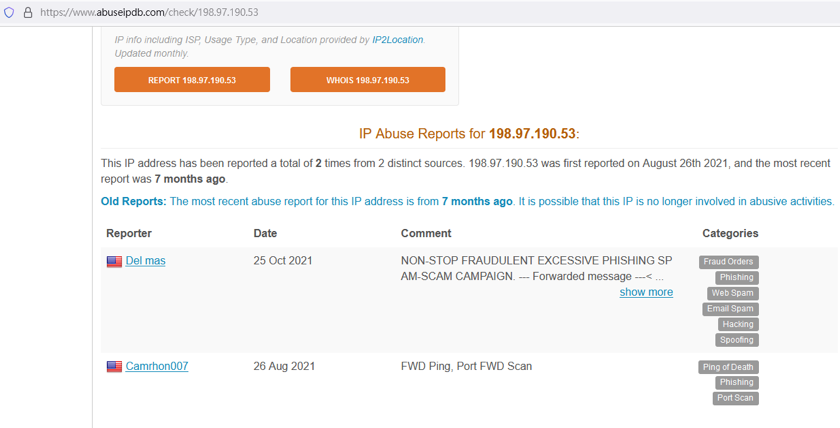
Diagram 3: Root DNS was reported to join cyber attacks
As mentioned, these types of attacking events are growing.
Conclusions
We are taught a lesson that digital signature is just one of the many factors to classify that the software may be trustworthy, but it should not be the only factor. Not only digital certificates stolen from known enterprises, we have identified that some malware is signed by valid digital certificates of governments. After investigating, we find that the governments have outsourced the codes to 3rd parties, and the 3rd parties accidentally leaked the digital certificates. This is one of the reasons why attackers can sign their own malware with these valid digital certificates.
“Whitelist” is a way to make things easier, but it can also be the weakest link in our infrastructure. Security teams shall pay extra attention to these types of breaches.
